A Comprehensive Web Application Security Checklist: 20 Best Practices
With web applications becoming more and more popular with each passing day and businesses developing their own apps, the number of hacking and information leak cases has also risen exponentially. The issue of web app security is a growing area of concern within the mobile industry after a number of high-profile data leaks. Not to mention the fact that malicious hackers are targeting applications with sophisticated attacks. Needless to say, application security is no longer optional; it has become an absolute necessity. Ensuring top-notch web application security for your web app and following web app security best practices are vital not only to enhance user experience but also to preserve and improve your business reputation.
Besides, if an application is vulnerable to risks, it won’t be able to serve the expected results to the users. It does not achieve success, and ultimately, your business goes downward. Even today, more than 50% of companies do not allow a separate budget for app security. While this means a threat to vicious hackers, it can be a huge risk for businesses. In order to ensure a higher download rate, you need to protect your app from common as well as severe damages that can lead to data loss.
Let’s get into the nitty-gritty and find out the web application security best practices that’ll help keep cyber attacks at bay.
Table of contents
- The Challenges of Maintaining Application Security
- Tools to Identify Vulnerabilities in Web Applications
- Web Application Security Checklist- 20 Best Practices
- Implement Robust Authentication
- Manage Access Controls
- Assets Tracking
- Update and Patch Regularly
- Perform Input Validation
- Data Encryption
- Use of HTTPS and TLS Encryption
- Implement DevSecOps
- Conduct Regular Security Scans
- Penetration Testing
- Perform Continuous Risk Assessment
- Leverage Virtual Patching
- Review Error Handling
- Choose Security Tools Wisely
- Secure Configuration and Deployment Practices
- Follow Proper Logging Practices
- Cross-Origin Resource Sharing
- Follow the Principle of Least Privilege
- Maintain Proper Report And Documentation
- Final Thoughts
The Challenges of Maintaining Application Security
Whether you are developing an E-commerce app or a business app, protecting your application from various security threats is vital, to say the least. Besides, a single security breach of stored data can lead to a significant loss of trust, financial repercussions, and even legal consequences. Moreover, reputation damage following a security breach can devastate a business.
According to various research and reports, mobile app security is getting more complex because of the rising threats.
The table below shows the percentage breakdown of types of cyber attacks on web applications.
| Types of Cyber Attacks | Percentage(%) |
| XSS (Cross-Site Scripting) | 25 |
| Information Leakage | 23 |
| Authentication and Authorization | 15 |
| Session Management | 13 |
| SQL Injection | 7 |
| CSRF | 6 |
| Other | 11 |
Nowadays, hackers have started creating advanced methods to take advantage of security flaws, steal confidential information, and jeopardize user privacy. Needless to say, keeping your application safe and secure can be a daunting task. Read on to find out the five common challenges that developers face when implementing web application security best practices into an app.
DDoS Attacks
Short for Distributed Denial of Services, DDoS attacks your system by flooding the applications, websites, or networks with high traffic, preventing users from accessing their web applications. Some examples of DDoS attacks that are more often employed by hackers to gain information about applications are HTTP Flood, NTP Amplification, SYN Flood, and Ping of Death.
Injection Flaws
One prominent cause of cyber threats is code injection flaws. These occur when you don’t filter the input before passing it through the SQL server or the browser. This gives attackers the opportunity to inject malicious code into the web application to obtain sensitive information and integrate viruses or other malicious activities.
Malicious Bots
Did you know that bots compose 42% of overall web traffic and that nearly two-thirds of that percentage is malicious? Malicious bots are a kind of malware designed to steal sensitive information and attempt fraudulent activities to gain access to the host’s system or application. They are often employed to spread malware, launch DDoS attacks, steal passwords, and spread spam to obstruct the normal functioning of other applications.
Improper Security Testing
Security testing is one of, if not the most important, web application security best practices and can make or break your application’s reliability. However, when it comes to conducting web application security testing, many businesses make the mistake of not employing the right tools at stages where they are needed. However, what they fail to realize is the fact that better utilization of a wide range of cyber security tools to pinpoint most of the vulnerabilities in the web application will make their web app safe and secure. Needless to say, web application security testing is crucial for strengthening digital systems against cyber threats. By following security principles and goals, organizations can improve their cybersecurity position and protect their assets efficiently.
Also Read: What are Mobile App Testing Services?
Insufficient Encryption Measures
When it comes to building an application with top-notch security, insufficient encryption measures often become the obstacle in protecting your codes, sensitive data, identity information, and user details in the application from getting stolen. To tackle this, you must employ proper data encryption techniques to protect your data from hackers and secure your organization’s information, like passwords and account details.
Tools to Identify Vulnerabilities in Web Applications
As software continues to become more complex and more integral for businesses, it also represents a significant vulnerability. In fact, web applications are the #1 attack vector for data breaches. Fortunately, businesses can use tools to identify the vulnerabilities. Web security testing tools are helpful in proactively detecting application vulnerabilities and safeguarding websites against malicious attacks. Here are the top five tools that’ll help you find vulnerabilities in your web applications:
- Nikto
Designed to detect various security vulnerabilities, Nikto is an open-source web application and web server scanner. With Nikto, you can not only test 6700 potential vulnerabilities but also can perform security checks for outdated softwares and application updates that are not easily recognizable.
- Burp Suite
One of the best open-source security testing tools to detect vulnerabilities by intercepting, scanning, and modifying HTTP requests, Burp Suite is an integrated platform for performing security testing of web applications. It is also helpful in determining vulnerabilities like SQL injection and cross-site scripting and has a robust security testing capability for multiple operating systems.
- Nuclei
Nuclei is an open-source tool that helps you perform customizable and fast vulnerability tests based on DSL and YAML. It uses templates that can scan DNS, TCP, SSH, HTTP, SSL, and many more and sends requests to targets to provide large-scale and quick vulnerability scanning.
- Owasp ZAP
A powerful tool that facilitates the identification of vulnerabilities in online applications, Owasp ZAP, helps developers and security professionals detect and find vulnerabilities in web applications. It performs various security functions such as passive scanning security requests, uses a web crawler to identify the web app’s structure, and uses dictionary lists to find files and folders on the web server.
Also Read:Alcohol Delivery App Development: Building a Safe and Compliant On-Demand Platform
Web Application Security Checklist- 20 Best Practices

With mobile apps expected to reach more than 183.7 billion installations globally, there has also been an increase in mobile app security threats. Today’s cyberattacks are highly sophisticated, requiring constant vigilance due to many unknown or emerging threats. These threats require a proactive approach to mobile application security.
To combat these threats, spending on securing web apps has increased by leaps and bounds as shown below.
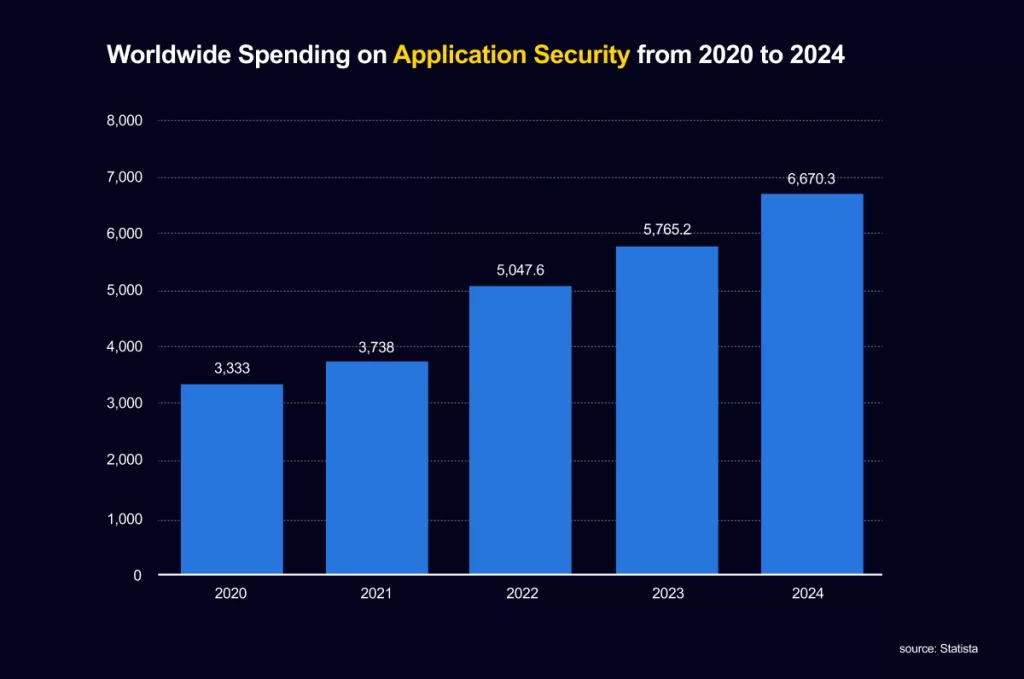
Securing a web app requires the regular review and improvement of existing security measures. Not to mention, you need to take into account a number of factors when implementing security measures for your web application. Listed below are the 20 best practices to keep your web application secure:
- Implement Robust Authentication
- Update and Patch Regularly
- Manage Access Controls
- Assets Tracking
- Perform Input Validation
- Data Encryption
- Use of HTTPS and TLS Encryption
- Implement DevSecOps
- Conduct Regular Security Scans
- Penetration Testing
- Perform Continuous Risk Assessment
- Leverage Virtual Patching
- Review Error Handling
- Use WAFs
- Choose Security Tools Wisely
- Secure Configuration and Deployment Practices
- Follow Proper Logging Practices
- Cross-Origin Resource Sharing
- Follow the Principle of Least Privilege
- Maintain Proper Report And Documentation
Implement Robust Authentication
In today’s digital landscape, robust authentication is the bedrock of any secure application. Not only does it act as a gatekeeper, verifying a user’s identity before granting access to sensitive data and functionalities, but it also protects unauthorized users from accessing your application. A lack of proper authentication measures will give an opportunity to the attacker to impersonate legitimate users and gain unauthorized access to your sensitive information, application, and data. To keep malicious attacks at bay, you can employ the following measures.
- Strong Password Policies: Apply strong password requirements and regular password changes for better protection of the users’ accounts.
- Multi-Factor Authentication (MFA): Enforce MFA to employ an additional layer of web application security by requiring users to complete multiple verifications.
- Password Storage: Implement robust salting and hashing methods to store passwords securely.
- Account Lookout Mechanism: Employ a robust account lookout mechanism to prevent users’ accounts from getting attacked by brute force.
Manage Access Controls
Also known as authorization, access control is a security technique that regulates who or what can view or use resources in a computing environment. Furthermore, access controls are designed to state who has permission to access specific data, functionalities, applications, and resources. It acts like a digital key to allow the right individuals to access the application but deny unauthorized access.
Not to mention, access controls also help protect your sensitive data, applications, resources, functionalities, intellectual property, and customer data. You must employ a zero-trust security model to check everyone and verify every time. This will ensure that there is zero unauthorized access to web applications and sensitive data.
Assets Tracking

In addition to implementing strong authentication methods and managing access controls, implementing asset tracking can also help make your web application secure and cyber threat-free. Asset tracking is a process of managing and monitoring the digital assets of a web application to determine the assets of the organization and remediate security gaps that are present and can be mitigated in time. Asset tracking helps reduce the possibility of cyber threats by minimizing the vulnerabilities of web applications and non-visible assets.
With asset tracking, you can not only keep track of your vulnerable features and resources that are left untouched, but can also reduce the untested assets, ultimately reducing the cost of hefty data breaches.
Update and Patch Regularly
Let’s face it, identifying security threats and vulnerabilities but not addressing them with the right security measures can leave your web application with security gaps. To make your web app free of vulnerabilities, you must employ necessary security updates and patches on a regular basis.
Security patches and updates are mandatory for any web application to work properly and without any threats. They often come with other updates like performance enhancements, graphics, and other feature updates. This will help you build robust application security that will keep hackers at bay.
Perform Input Validation

Input validation is regarded as the first line of defense in web application security and is prominently used to safeguard sensitive data, functionalities, and application resources. It is a security technique that ensures the data entered is as per the specifications and meets the validation criteria. You can prevent cross-scripting and injection attacks by employing input validation for users’ input data. Malicious attackers can target these kinds of vulnerabilities in your application quickly and get access to your sensitive data, but you can also prevent these attacks by implementing strong input validation in the front-end and back-end.
Input validation is often employed for web applications and websites to monitor the input data and check for formed data. There are multiple levels of validation, such as syntactic validation, where the input data, length, and types are validated, and semantic validation, where input data is checked for sense in the application context.
Data Encryption
Without a doubt, data encryption is a fundamental aspect of strong web app security as it not only helps protect people’s privacy but also secures data from attackers and other cybersecurity threats. Data encryption is a security method that translates plain text or data into incomprehensive text formats, such as ciphertext, which is only accessible to a person with a key or password. This helps protect your sensitive data from getting stolen and interpreted for manipulating the web application.
Data encryption is considered a powerful web application security best practice and helps protect your web application’s data and resources from cyber attacks and makes your web app more secure. Encrypted data can only be read once it is decrypted and turned back to plain text. This makes it hard for cyber attackers to steal and utilize your sensitive data, manipulate the application, and wreak havoc on your web application.
Use of HTTPS and TLS Encryption
In today’s day and age, HTTPS and SSL certificates are no longer optional—they’re essential for keeping data secure and building user trust. HTTP, or Hypertext Transfer Protocol Secure, is the standard protocol for WWW (World Wide Web) to build communication between the user’s computer and server through user searches. On the other hand, TLS (Transfer Layer Security) acts as part of HTTPS for encrypting and authenticating the standard protocol over the network to prevent vulnerabilities in web applications and also provide authentication, privacy, and data integrity over computer servers for multiple applications such as email, web browsing, and instant messaging. SSL/TLS uses certificates to establish encrypted communication between the client and server. Needless to say, this is an important web application security best practice and makes web browsing and assessing web applications more safe and secure.
Implement DevSecOps
It goes without saying that modern cloud environments have more moving parts, interdependent teams, and high-speed processes than ever. This complexity makes it difficult to implement security practices across the entire software development lifecycle (SDLC) and get the involved teams to participate consistently. This is the reason why securing modern-day development environments requires a DevSecOps approach: effective collaboration between security and DevOps, from code to production. DevSecops enables developers, security professionals, and operations specialists to integrate security features and testing into each phase of the web application development process.
Integrating the DevSecOps approach into your web application development process helps you identify the application’s vulnerabilities in an early stage and address them accordingly. This makes the application development process efficient and cost-effective.
Conduct Regular Security Scans
There’s no denying the fact that regular security scans are essential for maintaining a strong security posture. By consistently scanning your web application with automated tools, you can proactively identify vulnerabilities and misconfigurations that could be exploited by attackers. This allows you to address these weaknesses before they can be leveraged to compromise your application or data. Besides, the threat landscape is constantly evolving, so regular scans are vital for ensuring the ongoing security of your web application and staying ahead of emerging threats. It’s crucial to schedule these scans regularly and use a variety of scan types to ensure comprehensive coverage.
Penetration Testing
Often referred to as pen testing, penetration testing is the process of evaluating the security of the application by simulating a false cyber attack by using hacker-like tactics to exploit the vulnerabilities of the system. Not only does it protect users from cyber threats like data theft and leaks, but it also helps build trustworthy and legally compliant organizations. Needless to say, it’s an effective web application security best practice. With the help of penetration testing, you can find loopholes, security gaps, and vulnerabilities in the application more profoundly.
Also Read:Evolution of testing and importance of Manual Testing in modern times
Perform Continuous Risk Assessment

One of the crucial security measures that you can employ to keep your web application safe and secure is making sure you perform continuous risk assessment, where you conduct tests on a regular basis for risk analysis. This will help you identify the risk associated with your application, assess the intensity of the risk, and mitigate security risks in your web application. Not to mention, it can also help you to address all the potential threats that a hacker can exploit to access your sensitive information.
Performing risk assessments for your application also helps you keep track of all the potential threats and codebase vulnerabilities, prioritize resources, and build strategies that effectively mitigate risks in your web application. This ultimately strengthens your web application’s security posture.
Leverage Virtual Patching
Other than regular updates and patches, you can also employ virtual patching to protect your web application from cyber attacks. Virtual patching is a kind of security update that you employ without making any modifications to the source code or applying permanent changes. It provides an extra layer of security that helps developers get time to add security features, deploy changes, and test the patches themselves.
Virtual patching is often employed to leverage some time for developers to add security features when you are not able to release security updates, or immediate patches might disrupt normal operations. This technique is often employed with the help of security measures at the security perimeter, like WAFs and IPS. These security patches analyze the traffic, detect exploitable vulnerabilities, and provide an extra layer of security until permanent security updates or patches are released.

Review Error Handling
Improper handling of errors can introduce a variety of security problems for a web application. Needless to say, it is vital to review error handling accurately. Properly handling error messages provides pieces of information when something goes wrong during the employment security measures, and understanding the errors will help developers employ proper fixes in time and improve security in no time.
Improper error handling will bring threats and vulnerabilities to your web application, and if the error displayed to the end user conveys information on how your web application operates, it will create an opening for a cyber attack. These error messages help developers fix problems in the application but also enable hackers to have the opportunity to attack and steal sensitive information.
Use WAFs

A web application firewall, or WAF, is a security tool for monitoring, filtering, and blocking incoming and outgoing data packets from a web application or website. It helps protect your web application by monitoring and filtering the HTTP traffic between the internet and the web application. Furthermore, it also safeguards web applications from cyber attacks such as cross-site scripting, cross-site scripting, SQL injection, and file inclusion.
This attack mitigation method is commonly employed as a suite of tools that creates a holistic security framework together with other security measures to offset maximum types of attacks.
Choose Security Tools Wisely
When it comes to choosing security tools for your web app, it’s vital that you do proper analysis and research. The right tools can notably enhance your security posture. Consider incorporating Dynamic Application Security Testing (DAST) tools to simulate attacks on your running application, Static Application Security Testing (SAST) tools to analyze your source code for vulnerabilities, and Interactive Application Security Testing (IAST) tools to combine the benefits of both SAST and DAST. Additionally, employing a Web Application Firewall (WAF) will help you filter and monitor HTTP traffic, protecting your application from common threats. Furthermore, a multi-layered approach using a combination of tools tailored to your application’s specific needs is crucial for comprehensive security.
Secure Configuration and Deployment Practices
When deploying web applications, it’s crucial to implement secure configuration and deployment practices. This involves hardening your servers, configuring security settings correctly, and deploying applications with proper security measures. Additionally, automation tools should be considered to streamline the deployment process and reduce the risk of human error. Regularly review and update your configurations to align with the latest security recommendations. By adhering to these practices, you can minimize the attack surface and ensure a more secure deployment of your web application.
Follow Proper Logging Practices
Monitoring and logging activity on your web application is an effective web application security best practice and, helps identify potential security threats and provides valuable information for forensic investigations in the event of a security breach. By keeping a detailed log of each application event, it is easy to trace the steps of an attacker and seal the vulnerability from being exploited in the future.
To effectively follow proper logging practices, it’s essential to log the right information at the right level of detail. This includes logging user login attempts, access control decisions, data modifications, and system errors. Additionally, logs should be securely stored and regularly reviewed to identify any anomalies or potential security breaches.
Cross-Origin Resource Sharing
Cross-origin resource sharing (CORS) is a mechanism for integrating applications. CORS defines a way for client web applications that are loaded in one domain to interact with resources in a different domain. If you don’t utilize proper CORS practices, browsers will restrict these interactions due to the Same-Origin Policy, which is designed to prevent malicious scripts from accessing sensitive data. CORS provides a way to selectively enable cross-origin access while maintaining security.
When it comes to sharing resources and APIs while keeping security as a focus point, CORS plays a vital role because it is considered a set of HTTP headers that define how a web browser and a server can interact when they originate from different domains.
Follow the Principle of Least Privilege
Also known as the principle of minimal privilege (POMP) or the principle of least authority (POLA), the principle of least privilege states that users, processes, and systems should only have limited access to perform their functions. With the least privileged access, the user, whether an internal employee or a third-party vendor, is granted the minimal amount of access rights and privileges to only those who need it for a required job. This reduces the hacker’s attacks and will also limit the damage caused to your web application.
To implement the principle of least privilege, you must grant minimum permissions to your users required to perform the tasks and processes and also remove all unnecessary permissions. You must also limit users’ access to the web app’s sensitive data, like financial information and login credentials, to only authorized personnel.
Maintain Proper Report And Documentation
Last but certainly not least, make sure you maintain proper documentation and comprehensive reports, including but not limited to documenting security policies, procedures, incident response plans, and the results of security assessments and tests. Proper documentation ensures that security measures are consistently implemented, facilitates knowledge sharing among team members, and aids in compliance with regulatory requirements. Additionally, well-maintained documentation serves as a valuable resource for future reference, troubleshooting, and continuous improvement of your web application’s security measure.
Final Thoughts
With cyber threats growing at an exponential rate globally, keeping web applications safe and secure is no longer an option but a necessity for businesses. You can enforce security measures for your web application by ensuring secure coding and deployment, authentication, authorization, input validation, access control, and more for a cyber-threat-free user experience.
By adhering to the above-mentioned web application security checklist, you can fortify your web application against a wide range of cyber threats in no time.
Secure Tomorrow, Today with APPWRK
Want to build a high-quality web application with top-notch security? APPWRK, an app development, and AI-driven digital transformation company, can be your best bet. Our highly skilled and seasoned developers create highly secure apps by employing the best web application security practices. Leveraging years of experience, we integrate security measures in each and every stage of web app development and help mitigate vulnerabilities early.
With a commitment to quality and a security-first approach to building web applications, we leave no stones in terms of creating a safe and secure application at a price that’ll fit right into your budget. Contact Us now for your peace of mind and unmatched protection.
About author
Whether you are planning a start-up or want to enhance your existing business, APPWRK is a one-stop solution to satisfy your goals and expectations. We have action-oriented experience in UI/UX, Mobile, and Web App development. Also, you can knock on our door for Quality Assurance and Digital Marketing services.
Book A Consultation Now!






 Free Quote
Free Quote