15 Best Mobile App Security Threats and How to Prevent Them
As mobile applications become indispensable in our daily lives, they have also become prime targets for cybercriminals. Whether it’s financial transactions, personal communications, or business operations, mobile apps store and process vast amounts of sensitive data. However, this makes them vulnerable to various security threats, including data breaches, malware attacks, and unauthorized access. According to a report by Zimperium, over 83% of mobile applications have security vulnerabilities, exposing users and businesses to significant risks. These security flaws can lead to identity theft, financial fraud, and corporate espionage, making it critical to address them effectively.
To safeguard mobile apps from cyber attacks, developers, businesses, and users must take a proactive approach. From strong encryption that safeguards sensitive data to carefully vetting third-party integrations to prevent vulnerabilities, taking necessary steps to ensure the security of mobile apps is essential.
Let’s explore the biggest security threats mobile apps face and find actionable solutions to prevent them.
But before diving into the Best Mobile App Security Threats and How to Prevent Them, let’s first understand what mobile app security is.
Table of contents
- What is Mobile App Security?
- The Need For Mobile App Security
- 5 Reasons For Increased Security Threats To Mobile Apps
- 15 Common Mobile Application Security Threats
- 1. Malware Attacks
- 2. Unsafe Third-Party APIs
- 3. Weak Encryption
- 4. Data Leakage
- 5. Insecure Authentication
- 6. Insufficient Input/Output Validation
- 7. Overprivilaged Apps
- 8. Unsecure Third-Party Components
- 9 Unpatched Vulnerabilities
- 10. Insecure Network
- 11. Malicious Third-Party Code
- 12. App Permissions
- 13. Insecure Transport Layer Protection
- 14. Weak or Removed Server-Side Controls
- 15. Client-Side Injection
- 13 Strategies for Developing Secure Mobile Apps
- Increase User Authentication Security
- Ensure the Software Supply Chain is Secure
- Secure Data
- Ensure Safely Managed Sessions
- Use the Concept of Least Privilege
- Modify Your Testing Strategy
- Use App Shielding
- Always Remember the SSL Certificate
- Review Your API
- Encrypt the Data Required by Your Device
- Craft a Secure Code
- Implement File-Level & Database Encryption
- Secure the Backend
- How to Approach Mobile Application Security: Key Tips
- Keeping Your Mobile App Data Safe
- Mobile App Security FAQs
What is Mobile App Security?
Mobile app security refers to a collection of practices, protocols, and technologies aimed at protecting mobile applications from various cyber threats. Mobile application security safeguards mobile software from hacking attempts and malware infections, as well as data breaches and unauthorized intrusions made by malicious actors. People rely on mobile applications increasingly for their daily needs and work; therefore, mobile security measures have become the most essential requirement in modern times. Attackers use compromised mobile applications to harm sensitive user information and enable system network breaches through those same applications.
As mobile app security becomes more critical in protecting sensitive data, the global mobile application security market continues to grow in response to rising threats. Let’s take a closer look at this growth:
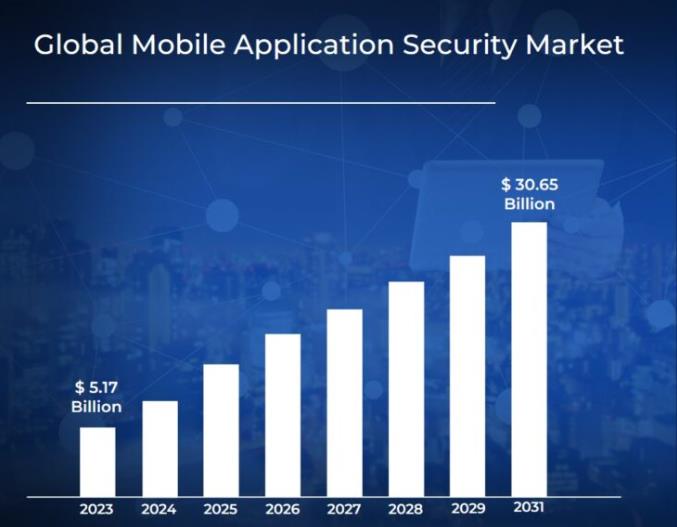
This growth highlights the increasing importance of mobile app security in today’s digital landscape, emphasizing the need for robust protection measures.
The Need For Mobile App Security
Over the years, cyber threats targeting mobile apps have grown exponentially as hackers continuously develop new techniques to exploit vulnerabilities, making it increasingly important to adopt robust security measures. Businesses and personal users remain at risk of experiencing detrimental effects through financial losses and identity theft, together with damage to their reputations, because of improper security standards. Attackers exploit mobile attacks through phony messages, commonly known as phishing, where they inject malicious software and manipulate application programming interfaces to break into app server systems and access user data on mobile devices.
Personal and login data theft
Many mobile applications require users to input personal details, such as phone numbers, full names, email addresses, and login credentials. When personal information remains insecurely stored or transmitted to and from systems, hackers can take advantage of these weaknesses and break in unauthorizedly.
Stolen Financial Data
Mobile banking apps, digital wallets, and e-commerce platforms have become essential pillars of modern life, processing a vast number of financial transactions every day. These apps store vast amounts of sensitive financial data, including credit card numbers, bank account details, and payment credentials, making them prime targets for cybercriminals. Attackers use techniques like keylogging, fake overlays, and malicious software to steal payment information from unsuspecting users.
Intellectual property theft
Businesses and developers spend a lot of time and resources developing proprietary mobile applications with unique software, algorithms, and user interfaces. However, if there is no proper security in place, hackers can easily reverse-engineer the apps to extract source code, proprietary business logic, or sensitive API keys.
Reputational damage
Let’s face it, one breach of security can forever change an app’s reputation. Users entrust companies with the handling of their personal and monetary information, and a breach in this can cause the organization to receive severe backlash. Negative and dismal reviews are likely to follow when users feel their information is not safe, and most will abandon the app.
5 Reasons For Increased Security Threats To Mobile Apps
There’s no denying the fact that mobile apps are increasingly being targeted by cybercriminals as their use grows across various industries. With more sensitive data being processed and new attack techniques emerging, the security risks to these apps are on the rise, making enhanced protection essential to safeguard both user data and app functionality.
1. Hackers taking advantage of app platforms
Mobile apps are distributed through various platforms, including the Apple App Store, Google Play Store, and third-party marketplaces. While Apple and Google enforce strict security policies, malicious apps can sometimes bypass these filters. Hackers often disguise harmful apps as legitimate software, tricking users into downloading malware-infected applications that steal data or spy on their activity.
2. Insecure data storage
Many mobile apps store sensitive user information, such as login credentials, user preferences, and payment details. However, improper storage practices can expose this data to cyber threats. For instance, storing data in plaintext files or unencrypted databases allows attackers to easily access it if they gain control of a device. Without encryption, attackers who gain access to the local database or app files can extract personal and financial details, leading to potential identity fraud and financial losses.
3. Communication vulnerabilities
Mobile apps frequently communicate with remote servers to send and receive data. If this communication is not properly secured, hackers can intercept sensitive information, manipulate transactions, or gain unauthorized access to user accounts. One of the biggest risks is the use of HTTP instead of HTTPS, as unencrypted connections expose data to man-in-the-middle (MITM) attacks.
4. Poor authentication procedures
Authentication plays a crucial role in protecting your app from unauthorized access, but poor authentication practices can easily compromise your security. Simple passwords or weak session management invite hackers to exploit vulnerabilities using methods like brute-force attacks or credential stuffing.
5. Inadequate data encryption
Data encryption is vital for safeguarding sensitive user information, but inadequate encryption methods expose apps to severe risks. When data is not properly encrypted, hackers can intercept or steal it during transmission or access it when stored on the device. This is especially dangerous for apps handling personal, financial, or healthcare data.

15 Common Mobile Application Security Threats
Mobile app security is essential for protecting sensitive user data from a wide range of threats that could jeopardize privacy and disrupt functionality. Both developers and users must be aware of these security risks to defend against malicious activities effectively. Below, we outline the top 15 mobile app security threats and offer strategies to mitigate them.
1. Malware Attacks
Malware attacks are one of, if not the most, common and damaging threats to mobile app security. These malicious software programs can infect apps through downloads, phishing attacks, or unsafe third-party app stores, leading to data theft, system damage, or unauthorized access. Malware is often disguised as legitimate apps or software, making it easy for unsuspecting users to download.
2. Unsafe Third-Party APIs
Even though using third-party APIs in mobile apps can accelerate development, they can also introduce significant security vulnerabilities. Unsafe third-party APIs can expose apps to various risks, such as unauthorized data access, data leaks, and exploitation of app weaknesses. Malicious third-party APIs can enable attackers to bypass security measures, allowing them to gain access to user data or the app’s back-end systems.
3. Weak Encryption
Weak encryption is a significant mobile app security risk that can expose sensitive data to attackers. If encryption protocols are not strong enough, it becomes easier for hackers to intercept or decrypt user data, particularly when it is transmitted over unsecured networks. Weak encryption can lead to severe breaches of user privacy, such as the theft of personal, financial, or health-related information.
4. Data Leakage
One of the most common mobile security threats, data leakage, happens when sensitive user information is unintentionally exposed due to weak security protocols or flawed coding. This can occur through insecure data storage, unprotected app logs, or improper handling of personal data. Besides, hackers often target leaked information for identity theft, fraud, or unauthorized access, leading to severe privacy violations and legal consequences.
5. Insecure Authentication
With weak authentication mechanisms in place, mobile applications become an easy target for attackers seeking unauthorized access to sensitive data. Many apps still rely on single-factor authentication, such as passwords, which are highly vulnerable to brute-force attacks and credential stuffing. Without additional security layers like multi-factor authentication (MFA) or biometric verification, hackers can easily exploit these weaknesses.
6. Insufficient Input/Output Validation
Failing to properly validate user input and output data creates significant security risks in mobile applications. Attackers exploit this weakness to inject malicious code, execute unauthorized commands, or access sensitive information. Without strict validation, apps become vulnerable to SQL injection, cross-site scripting (XSS), and buffer overflow attacks, which can compromise user data and system integrity. Unchecked input can also lead to crashes, performance issues, and unintended behavior, making the app unstable and unreliable.
7. Overprivilaged Apps
While app permissions are necessary for functionality, granting excessive access can create serious security vulnerabilities. Some mobile applications request permissions beyond what is needed, such as accessing contacts, location, or the microphone without a clear purpose. These unnecessary privileges increase the attack surface, allowing hackers to exploit them for data breaches or unauthorized surveillance. To enhance security, developers should adhere to the principle of least privilege, ensuring apps only request the essential permissions required for their intended operations.
8. Unsecure Third-Party Components
Unsecure third-party components, such as libraries, frameworks, and SDKs, can introduce vulnerabilities into mobile apps if they are not properly vetted or maintained. Many developers rely on third-party code to speed up development, but using outdated or insecure components can expose the app to potential exploits. Attackers often target known vulnerabilities in third-party libraries, gaining unauthorized access to the app or its data.
9 Unpatched Vulnerabilities
Unpatched vulnerabilities are one of the leading causes of security breaches in mobile apps. Developers who fail to update their apps with the latest security patches are exposed to attacks that exploit known flaws. Whether it’s an outdated operating system, a third-party component, or a vulnerability within the app itself, unpatched security gaps provide hackers with opportunities to infiltrate the system and compromise user data.
10. Insecure Network
Public and unencrypted Wi-Fi networks pose a major risk to mobile app security, making it easier for attackers to intercept data transmissions. Hackers can exploit these unsecured connections to launch man-in-the-middle (MITM) attacks, eavesdrop on sensitive information, or inject malicious code into app communications. Without proper encryption, user credentials, payment details, and private messages become vulnerable to unauthorized access.
11. Malicious Third-Party Code
Malicious third-party code is a significant threat to mobile app security, often introduced through third-party libraries, SDKs, or external plugins. Developers commonly use these components to accelerate development and add features, but if they come from unverified sources, they can introduce vulnerabilities or hidden malware into an app.
12. App Permissions
Granting excessive app permissions poses a serious security risk by exposing sensitive user data to potential abuse. Many apps request access to device features such as the camera, microphone, contacts, location, and storage, often beyond what is necessary for functionality. Attackers can exploit overprivileged apps to harvest personal information, track user activity, or execute unauthorized actions.
13. Insecure Transport Layer Protection
Insecure transport layer protection occurs when data transmitted between a mobile app and a server is not adequately encrypted, making it vulnerable to interception and manipulation by attackers. Unprotected data transmission can lead to man-in-the-middle (MITM) attacks, where hackers eavesdrop on or alter sensitive information such as login credentials and payment details.
14. Weak or Removed Server-Side Controls
Server-side security is crucial in protecting mobile applications, yet many apps suffer from weak or improperly configured server-side controls. Attackers often target these vulnerabilities to bypass authentication, escalate privileges, or access backend databases. Common issues include improper input validation, lack of rate limiting, and outdated security patches.
15. Client-Side Injection
Client-side injection vulnerabilities occur when an attacker injects malicious scripts or code into a mobile app, exploiting weaknesses in input validation and execution. This can lead to cross-site scripting (XSS), SQL injection, or command injection attacks, allowing attackers to steal user data, manipulate app behavior, or gain unauthorized access.
13 Strategies for Developing Secure Mobile Apps
In today’s fast-paced digital world, ensuring the security of mobile applications is paramount to protect user data and maintain trust. A secure mobile app is built through continuous vigilance, robust design, and effective implementation of security measures throughout its development lifecycle. The strategies outlined below highlight essential steps developers should take to enhance the security of their mobile applications.
Increase User Authentication Security
User authentication is a critical aspect of mobile app security, as it controls access to sensitive information. Weak authentication mechanisms, such as simple passwords, can be easily exploited by attackers. To increase user authentication security, developers should implement multi-factor authentication (MFA), requiring users to provide two or more forms of verification, such as a password combined with a biometric scan or one-time passcode.
Ensure the Software Supply Chain is Secure
The security of the software supply chain is a crucial yet often overlooked aspect of mobile app development. Third-party libraries, frameworks, and tools commonly used in mobile apps can introduce security risks if not properly vetted. An insecure or outdated third-party component could serve as an entry point for attackers, leading to vulnerabilities or malware infiltration.
Secure Data
Securing data is one of the most important aspects of mobile app security. Sensitive user information, such as personal data, financial details, and login credentials, can be a prime target for attackers. Developers must ensure that data is encrypted both at rest (when stored) and in transit (during transmission).
Ensure Safely Managed Sessions
Session management plays a crucial role in mobile app security, particularly when it comes to preventing unauthorized access to user accounts. Insecure session management can lead to session hijacking, where attackers intercept or steal a user’s session token, granting them unauthorized access to the app.
Use the Concept of Least Privilege
The principle of least privilege (PoLP) is an essential security strategy that limits users’ access rights to only the minimum necessary resources for them to perform their tasks. Applying this concept within a mobile app means that each app feature, service, or API should only have access to the data or functionality required for its intended purpose.
Modify Your Testing Strategy
Security testing is an integral part of the mobile app development process. However, many developers still rely on basic testing strategies that focus on functionality rather than security. To ensure a mobile app is secure, developers must modify their testing strategy to include a variety of security testing techniques, such as penetration testing, vulnerability scanning, and code reviews.
Use App Shielding
App shielding is a proactive security measure that adds an additional layer of protection to mobile applications. It involves the use of technologies that prevent reverse engineering, tampering, and decompiling of the app’s code. By shielding an app, developers make it more difficult for attackers to gain insights into the app’s functionality or exploit vulnerabilities.
Always Remember the SSL Certificate
While mobile apps frequently exchange sensitive data, failing to secure these transmissions can expose users to cyber threats like data interception and man-in-the-middle (MITM) attacks. Implementing SSL/TLS certificates ensures that all communication between the app and its servers is encrypted, keeping user data secure.
Review Your API
Whether an app relies on internal or third-party APIs, weak security measures can leave it vulnerable to attacks such as unauthorized access, data leaks, and injection attacks. Ensuring strong authentication and authorization mechanisms for API requests is essential in preventing breaches.
Encrypt the Data Required by Your Device
Since mobile devices store critical user information such as login credentials, payment details, and personal preferences, weak encryption can expose this data to cybercriminals. Encrypting all locally stored data using advanced cryptographic algorithms like AES-256 ensures that even if an attacker gains access to the device, the information remains unreadable.
Craft a Secure Code
Without proper security measures in place, mobile applications can become easy targets for attackers looking to exploit vulnerabilities. Writing secure code from the start is crucial in reducing the risk of security breaches. Developers should follow best practices such as input validation, code obfuscation, and error handling to minimize attack vectors.
Implement File-Level & Database Encryption
Even when an app enforces strong authentication, unencrypted files and databases can still pose security risks. Sensitive data stored within the app must be encrypted using industry-standard encryption algorithms like AES-256 to prevent unauthorized access. File-level encryption ensures that even if an attacker gains access to stored files, they remain unreadable.
Secure the Backend
Since backend systems manage and store vast amounts of user data, weak security can create significant vulnerabilities, leading to breaches. Encrypting all data at rest ensures that even if attackers gain access to the database or file system, they cannot read the sensitive information. Enforcing strict authentication measures, such as multi-factor authentication (MFA) and role-based access control (RBAC), helps prevent unauthorized users from accessing backend resources.
How to Approach Mobile Application Security: Key Tips
Securing mobile applications requires a proactive approach from the very beginning. It’s crucial to implement secure coding practices early on to prevent vulnerabilities like SQL injection, buffer overflows, and cross-site scripting. Additionally, conducting regular code audits and testing throughout the development process helps identify and address potential weaknesses before they become major issues.
Here are four tips to help secure your mobile applications:
- Use Strong Encryption: Encrypt sensitive data both at rest and in transit to protect user information from unauthorized access.
- Implement Multi-Factor Authentication: Adding an extra layer of security helps prevent unauthorized access, even if login credentials are compromised.
- Secure Third-Party Integrations: Carefully vet and secure all third-party services and libraries integrated into your app to prevent introducing vulnerabilities.
- Keep Software Up to Date: Regularly update your app and underlying infrastructure to patch known security vulnerabilities and improve defenses against emerging threats.
Keeping Your Mobile App Data Safe
Securing mobile app data is a multifaceted challenge that involves both technological and operational strategies. With the increasing threats to app security, it’s crucial to implement the right measures from the start. Are you looking to develop a secure mobile app? Look no further than APPWRK IT Solutions. We specialize in developing secure mobile applications that adhere to the best security practices. Our team helps businesses protect their sensitive data by implementing strong encryption protocols, robust authentication, and continuous security testing. We offer tailored solutions to meet your app security needs, ensuring your data stays safe from evolving cyber threats.

For expert assistance in developing highly secure mobile apps, contact us today. Let us help you build a mobile app that prioritizes security, giving you peace of mind and keeping your users’ data safe.
Mobile App Security FAQs
How do you ensure the security of a mobile application?
To ensure the security of a mobile application, start by incorporating secure coding practices and robust encryption methods. Regular penetration testing, code reviews, and updates will help identify and fix vulnerabilities. Additionally, implementing multi-factor authentication and secure APIs strengthens the app’s defenses.
What are the three main ways to prevent security threats?
The three primary ways to prevent security threats are:
- Implementing strong encryption for data at rest and in transit.
- Using secure APIs and third-party libraries to prevent vulnerabilities.
- Adopting multi-factor authentication to secure access to sensitive data and functionality.
What are common security risks associated with mobile applications?
Common security risks include data breaches, weak authentication, insecure network connections, improper session handling, and insecure APIs. These vulnerabilities can lead to the exposure of sensitive user information or allow attackers to manipulate app functionality.
What are some of the major privacy security threats related to the use of mobile apps?
Privacy threats in mobile apps can include unauthorized data collection, inadequate data storage protection, and insufficient transparency about data usage. Additionally, mobile apps that don’t comply with privacy regulations can expose users to risks related to personal information being shared without consent.
Are AI and Application Security Friends Or Enemies?
AI can be both. It strengthens security by automating threat detection and identifying vulnerabilities quickly. However, cybercriminals can also use AI for attacks. The key is to use AI responsibly to enhance security while being aware of its potential risks.
About The Author





 Free Quote
Free Quote