How to Perform Mobile App Security Testing
With mobile applications becoming more and more popular with each passing day and businesses developing their own apps, the number of hacking and information leak cases have also risen exponentially. The issue of mobile application security is growing area of concern within the mobile industry after a number of high-profile data leaks. Not to mention the fact that, malicious hackers are targeting on applications with sophisticated attacks. Needless to say, application security is no longer optional; it has become an absolute necessity.
In fact, a recent study shows that almost 60% of users stop using an app if they come across security issues within the application. Needless to say, ensuring top-notch mobile application security for your business app is vital not only to enhance user experience but also to preserve and improve your business reputation. Besides, if an application is vulnerable to risks, it cannot serve the expected results to the users. It does not achieve success, and ultimately, your business goes downward. Even today, more than 50% of companies do not allow a separate budget for app security. While this means a threat to vicious hackers, it can be a huge risk for businesses. In order to ensure a higher download rate, you need to protect your app from common as well as severe damages that can lead to data loss.
Let’s find out more about mobile application security testing, what it is and the best practices for performing it.
Table of contents
- What Is Mobile Application Security Testing?
- Mobile Apps Hacking Statistics
- The Importance of Mobile App Security Testing
- Common Mobile App Security Threats
- Understanding Mobile App Security Issues: Android vs iOS
- Principles of Secure Mobile App Development
- Types of Mobile App Security Tests
- How to Conduct Security Testing in Mobile Applications?
- Techniques for Security Testing in Mobile Apps
- Best Practices in Mobile App Security Testing
- Tools for Securing Mobile Applications in a CL Pipeline
- Automating Mobile Security Tests with Continuous Integration
- How an Advanced Testing Platform Can Help
- Too complex for you? Hire APPWRK
- What is the criteria for mobile application security testing?
- What are the development fall-outs in mobile application protection?
- How to check if a mobile app is secure?
- What is SAST and DAST for mobile apps?
- How do I check the security of an application?
- How to test mobile apps manually?
What Is Mobile Application Security Testing?
Mobile application security focuses on ensuring the security posture of apps across various platforms, including Android, iOS, and Windows Phone. It applies to applications running on both mobile phones and tablets and assessing them for vulnerabilities based on the platforms they operate on, the frameworks used in their development, and their intended user base. Given the fact that mobile apps play a vital role in any business’s online presence and, for some, serve as the primary source of income, mobile app security testing is highly essential.
Mobile Apps Hacking Statistics
In recent years, mobile apps have become the prime targets for hackers, and their vulnerabilities are more significant than most people realize. With mobile app usage constantly being on an incline, cybercriminals are actively seeking new ways to exploit its weaknesses, whether it is through malicious code, malware, or vulnerabilities in the app’s codebase. Here are some eye-opening statistics that highlight the importance of mobile app security testing:
- 76% of mobile apps have at least one serious security vulnerability, putting user data at risk.
- 43% of cyberattacks now target mobile apps, as hackers exploit weak security measures.
- 82% of Android apps and 65% of iOS apps have security flaws related to insecure data storage and weak encryption.
- One in four mobile applications contains at least one high-risk security flaw.
- 50% of apps with five to ten million downloads include a security flaw.
The Importance of Mobile App Security Testing
Even if your mobile app has the most robust features and a highly captivating interface, without proper security, you risk losing it all to malicious attacks and data thefts. Security concerns not only sabotage your business but also harm the users of your app, leaving them with a bad impression and abandoning your app altogether. Here are the some alarming statistics that reveal the biggest security concerns among users.
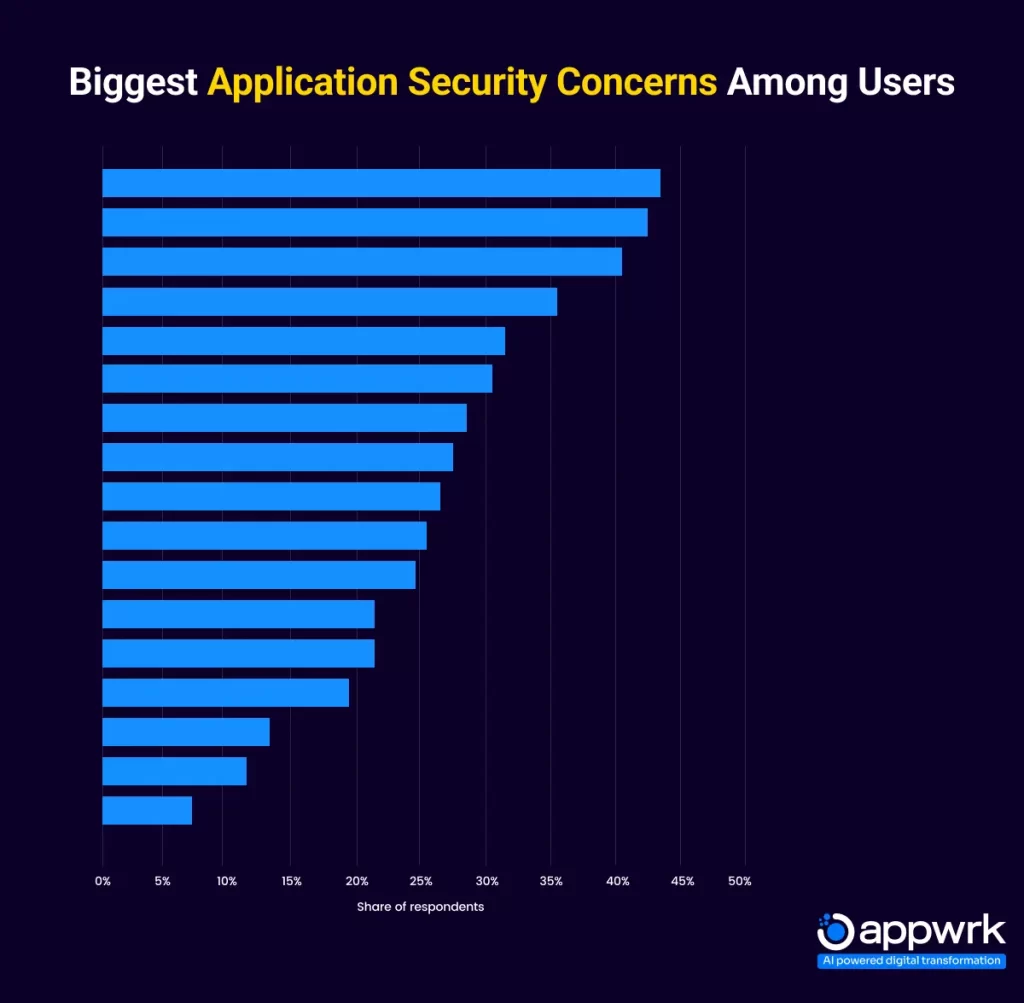
Mobile app security testing is crucial not only to safeguard your user’s data but also to ensure that you maintain business integrity and prevent financial losses and hence many companies have started incorporating it to their development and post-launch maintenance cycles. In fact, according to a recent market research, the global Mobile Application Security Testing (MAST) Market was valued at USD 0.9 billion in 2023 and is projected to grow at a CAGR of 28.3%, reaching USD 3.2 billion by 2028.
By giving much emphasis to mobile app security testing, you can identify and fix weaknesses in authentication, encryption, data storage, and network communication before attackers can exploit them. In addition to that, adhering to security regulations such as GDPR, CCPA, and PCI DSS ensures that your app meets legal and industry standards, avoiding costly fines and maintaining user trust.
Common Mobile App Security Threats
Whether you currently own a mobile application or are in the process of developing one, it is extremely crucial to be aware of the most common mobile app security threats. By understanding these threats, you will be able to anticipate the potential vulnerabilities and implement preventive measures, helping you stay one step ahead of cyber attackers. Here are some of the most prevalent mobile app security threats that you should be vigilant about:
- Insecure Data Storage:
Sensitive user data stored without proper encryption can be easily accessed if the device is compromised.
- Weak Authentication & Authorization:
Poorly implemented login mechanisms make it easier for attackers to gain unauthorized access.
- Insecure API Communication:
Unprotected APIs can expose user data and app functionality to cyber threats like man-in-the-middle (MITM) attacks.
- Code Injection Attacks:
Hackers can exploit vulnerabilities in the app’s code to execute malicious scripts or commands.
- Reverse Engineering:
Attackers can decompile an app’s code to discover security flaws, extract sensitive information, or modify app behavior.
- Malware & Trojan Attacks:
Malicious software can be injected into apps to steal data, spy on users, or compromise device security.
Understanding Mobile App Security Issues: Android vs iOS
Given the fact that Android and iOS have different development structures and vulnerabilities, they propose unique challenges. Since Android is open-source, it allows greater customization but also makes it more vulnerable to malware, unauthorized app installations, and fragmented security updates across different manufacturers.
On the other hand, the iOS ecosystem is more tightly controlled, with strict app review processes and consistent updates. While this reduces the risk of malware, it is still vulnerable to threats like zero-day and jailbreaking exploits. Here is a table that compares their securities under important areas:
| Security Factor | Android | iOS |
| App Distribution | Open app stores & third-party APKs increase malware risks | Strict App Store policies minimize malicious app distribution |
| Security Updates | Fragmented updates; some devices don’t receive patches | Centralized updates ensure better security coverage |
| Malware Risk | Higher risk due to sideloading & lack of strict app screening | Lower risk but still vulnerable to phishing & targeted exploits |
| Customization Risks | More freedom in modifying OS, leading to security loopholes | Limited customization reduces potential security gaps |
| Jailbreaking/Rooting | Rooting exposes devices to privilege escalation attacks | Jailbreaking can bypass Apple’s security controls, leading to vulnerabilities |

Principles of Secure Mobile App Development
No matter what the reason is, any compromise in mobile apps security can lead to disastrous events. Especially if your application handles payments, having stringent protocols is non-negotiable at any cost. In order to defend your application against these issues properly, you need to follow all the necessary principles at every stage of your app development lifecycle. Here are some of the key principles to implement:
- Secure Code Practices:
Writing clean, well-structured code with security in mind is essential to building a robust mobile application. Developers should avoid practices like hardcoding sensitive credentials, as this opens the door for potential exploits. Additionally, it’s important to guard against common vulnerabilities such as buffer overflows, which can be a gateway for attackers to manipulate the app. By following secure coding practices, developers can prevent many common attack vectors from the outset.
- Data Encryption & Strong Authentication:
Encrypting sensitive data both at rest and in transit is critical for protecting user information from unauthorized access. Strong cryptographic algorithms ensure that even if data is intercepted, it remains unreadable to attackers. Alongside encryption, implementing multi-factor authentication (MFA) and role-based access control (RBAC) adds layers of security, enhancing user identity verification and controlling access based on roles within the system. These measures reduce the likelihood of unauthorized access to both personal data and critical application functions.
- Secure API Communication & Regular Security Testing:
To prevent unauthorized access and data interception, secure protocols like HTTPS and OAuth should be used for API interactions. These protocols encrypt communication, safeguarding the app’s data flow. Furthermore, regular security testing is key to ensuring the app remains resilient to new threats. Mobile app pentesting testing, static and dynamic code analysis, and vulnerability assessments help identify and mitigate risks before they can be exploited. Integrating security testing throughout the development process ensures that vulnerabilities are caught and addressed proactively.
Types of Mobile App Security Tests
When it comes to mobile app security testing, there are various ways to go about it, with each offering its own unique capabilities. By utilizing these different testing approaches, you can uncover the vulnerabilities across all aspects of your app and enhance its overall defense against potential malicious attacks. Here’s a breakdown of key security testing types:
- Vulnerability Scanning:
Automated tools scan the app’s code, dependencies, and network interactions to detect security weaknesses, misconfigurations, or outdated libraries.
- Penetration Testing:
Ethical hackers simulate real-world attacks to identify exploitable vulnerabilities and assess the app’s resilience against cyber threats.
- Risk Assessment:
Evaluate the potential impact of security threats based on app architecture, data sensitivity, and threat exposure, helping prioritize mitigation strategies.
- Security Posture Assessment:
A comprehensive review of the app’s overall security framework, policies, and compliance with industry standards to ensure robust defense mechanisms.
How to Conduct Security Testing in Mobile Applications?
Now that we’ve covered the fundamentals of mobile app security testing, the next crucial step is understanding how to actually conduct these tests within mobile applications. This phase is arguably the most important, as it directly impacts the app’s ability to protect sensitive user data and prevent security breaches. Here’s a step-by-step guide to performing security testing in mobile applications:
1. Planning and Analysing Requirements
Before you get into conducting security testing for your mobile application, the first step is to understand the app’s architecture, user base, and potential security risks. You need to define the security testing objectives, choose the app security testing tools and frameworks, and assess the app’s functionality, platform, and dependencies to create a clear testing strategy.
2. Setting Up the Testing Environment
Next, you need to work on establishing a controlled testing environment that mimics real-world scenarios, including mobile devices, OS versions, and network conditions. For this, you can set up tools for vulnerability scanning, static analysis, and penetration testing to conduct tests in an isolated environment without affecting production data.
3. Conducting Static Analysis (SAST)
When it comes to reviewing an app’s source code and binaries before execution, conducting Static Application Security Testing (SAST) is key. This helps identify vulnerabilities like hardcoded credentials, insecure data handling, and code flaws before the app runs, allowing for early detection of security issues.
4. Performing Dynamic Analysis (DAST)
In order to evaluate your app’s runtime behavior and how it interacts with APIs, networks, and databases. Dynamic Application Security Testing (DAST) evaluates the app’s runtime behavior and interactions. This test uncovers vulnerabilities related to how the app operates in real time, such as insecure communication or improper session management.
5. Executing Penetration Testing
Mobile application penetration testing simulates an attack on the app to exploit identified vulnerabilities. Ethical hackers attempt to bypass security measures and gain unauthorized access, assessing the app’s resistance to potential cyber threats and determining the risk of real-world exploitation.
Techniques for Security Testing in Mobile Apps
Security testing in mobile apps is crucial to ensure that the application is secure, performs well under stress, and protects sensitive data. Here are several key techniques used in security testing for mobile apps:
API Security Testing
Since mobile apps rely on APIs to communicate with servers, ensuring API security is crucial. Test for common vulnerabilities like SQL injection, broken authentication, and improper access controls.
Reverse Engineering
Reverse engineering involves decompiling the app and inspecting its code, libraries, and binaries. It can uncover hardcoded sensitive information, security misconfigurations, and potentially insecure app logic.
Threat Modeling
Threat modeling involves identifying potential security risks early in the design phase. This helps determine possible attack vectors and assess security threats based on app functionality and infrastructure.
Network Security Testing
This involves testing the network communication between the mobile app and backend servers to ensure secure data transmission. Look for vulnerabilities like man-in-the-middle attacks (MITM), lack of SSL/TLS encryption, or weak ciphers.
Data Storage and Data Leakage Testing
Mobile apps store data locally on the device, which can be a target for attackers. This technique involves testing for improper storage practices (e.g., storing sensitive data in plain text) and ensuring sensitive data is adequately encrypted.
Best Practices in Mobile App Security Testing
- Start with Threat Modeling
Threat modeling helps identify potential security risks at the design stage of development. By analyzing the app’s architecture, user flows, and data interactions, you can pinpoint vulnerabilities early. This proactive approach allows you to mitigate risks before they become a problem, focusing testing efforts on the most critical areas.
- Conduct a Comprehensive Security Assessment
A thorough security assessment tests all areas of the app’s infrastructure, including code, data storage, network communication, and APIs. This process involves both automated tools (SAST, DAST) and manual penetration testing, ensuring that no vulnerability goes unnoticed across all attack vectors.
- Secure Data Storage
Ensuring sensitive data is stored securely on the device is essential to protecting user privacy. Encryption should be applied both to data at rest (stored locally) and in transit (while being transmitted over the network). Use platform-native secure storage mechanisms like iOS Keychain or Android Keystore for added protection.
- Secure Communication
Secure communication prevents man-in-the-middle (MITM) attacks by using encrypted connections (SSL/TLS) for all app-server communications. SSL certificate pinning can be implemented to further protect against compromised certificates, ensuring that the app only connects to trusted servers.
- Test for Weak Authentication and Authorization
Authentication and authorization mechanisms must be robust to prevent unauthorized access. This includes enforcing strong password policies, using multi-factor authentication (MFA), and ensuring users can only access resources and data they are authorized to view, applying role-based access controls (RBAC).
- Validate Inputs and Prevent Injection Attacks
Proper input validation is key to preventing injection attacks, such as SQL injection and XSS. By sanitizing and validating user inputs (including forms, URL parameters, and cookies), you minimize the risk of malicious code being executed within the app, thereby protecting both the app and the server.
- Leverage Code Obfuscation
Code obfuscation makes it harder for attackers to reverse-engineer the app and identify vulnerabilities. By using tools like ProGuard for Android or Xcode obfuscation for iOS, sensitive information, and app logic are concealed, reducing the likelihood of exploitation if the app is compromised.
- Perform Reverse Engineering and Malware Analysis
Reverse engineering allows you to evaluate how easily the app can be tampered with by decompiling the APK or IPA file. This helps identify hidden vulnerabilities, such as hardcoded secrets or weak encryption, and exposes potential attack vectors, ensuring these risks are addressed before release.
- Test for Platform-Specific Vulnerabilities
Both iOS and Android have unique security features and risks. Testing for platform-specific issues—like permissions on Android or sandboxing on iOS—ensures your app adheres to the platform’s security model and minimizes the potential for exploitation specific to that operating system.
- Protect Against Data Leakage
Preventing data leakage protects sensitive information on mobile devices from unauthorized access, especially in case of theft. By implementing secure data storage practices and clearing sensitive data from memory after use, you reduce the chances of attackers exploiting exposed information.
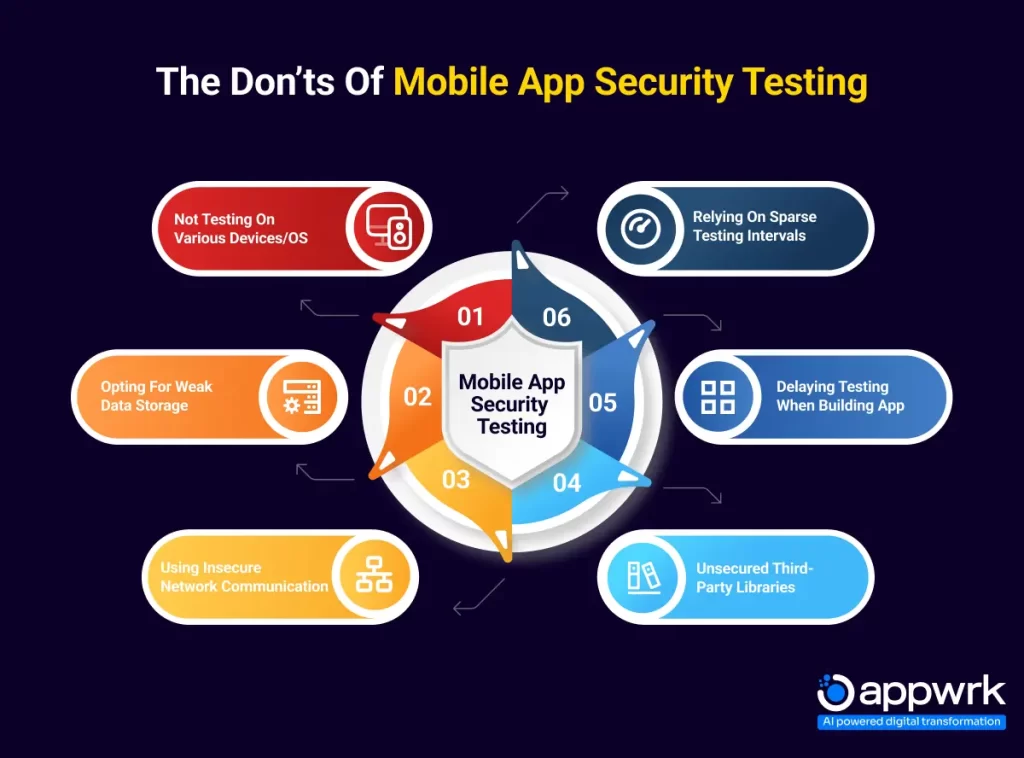
The Don’ts of Mobile App Security Testing
Tools for Securing Mobile Applications in a CL Pipeline
Securing mobile applications within a CI/CD pipeline is crucial to maintaining robust security throughout the development process. Tools like Static Application Security Testing (SAST) tools (e.g., SonarQube and Checkmarx) help identify vulnerabilities early by scanning the source code for security flaws.
Dynamic Application Security Testing (DAST) tools like OWASP ZAP and Burp Suite assess running apps, identifying runtime vulnerabilities. For mobile-specific security, tools like MobSF and Frida can test both Android and iOS apps for issues such as data leakage or weak encryption. Integrating these tools into CI/CD workflows, such as Jenkins or GitLab CI, automates security testing, ensuring vulnerabilities are detected and addressed before deployment.
Automating Mobile Security Tests with Continuous Integration
Automating mobile security tests with Continuous Integration (CI) is a crucial practice to ensure that security vulnerabilities are identified and addressed continuously throughout the development lifecycle.
By integrating security testing tools into the CI pipeline, teams can automate the detection of common vulnerabilities in mobile apps, such as insecure data storage, broken authentication, or exposure to malicious attacks.
Tools like OWASP ZAP (for dynamic security testing) and SonarQube (for static code analysis) can be integrated into CI systems such as Jenkins, GitLab CI, or CircleCI, allowing automated scans to run every time code is pushed, ensuring that security is consistently evaluated as part of the build process.
How an Advanced Testing Platform Can Help
An advanced testing platform can significantly enhance security for mobile applications by offering a comprehensive suite of tools and capabilities that streamline and automate the testing process. These platforms provide a centralized environment for running a variety of security tests, from static and dynamic code analysis to vulnerability scanning and penetration testing.
By integrating advanced testing tools like MobSF, OWASP ZAP, or Veracode into a single platform, teams can identify and address security risks across multiple layers of the app, including code, runtime behavior, and third-party dependencies. This enables teams to catch vulnerabilities early in the development cycle and apply fixes before the app is deployed to users, reducing the risk of security breaches.
Conclusion
Mobile app security testing is essential in today’s digital landscape, where cyber threats are constantly evolving. By identifying vulnerabilities before attackers do, businesses can protect sensitive user data, ensure compliance with security regulations, and maintain trust. Prioritizing security testing throughout the development lifecycle ensures that your mobile app remains resilient against cyber threats. By leveraging the right tools and best practices, businesses can deliver secure and seamless experiences to their users.

Too complex for you? Hire APPWRK
Worried about your mobile app’s security? APPWRK IT Solutions has you covered! We specialize in developing secure mobile applications that follow industry best practices, protecting your business from cyber threats. Our team implements strong encryption, robust authentication, and continuous security testing to keep your sensitive data safe. With tailored security solutions, we ensure your app stays resilient against evolving threats. Contact us today to build a mobile app that prioritizes security and gives you peace of mind!
FAQs
What is the criteria for mobile application security testing?
Mobile application security testing must cover several critical areas, including data protection, authentication, authorization, network security, and vulnerability assessment. The testing process should ensure that sensitive user data is encrypted, secure authentication mechanisms are in place, APIs are well-protected, and the app does not expose vulnerabilities to cyber threats. Compliance with industry standards like OWASP Mobile Security Testing Guide (MSTG) and adherence to security best practices also form key criteria.
What are the development fall-outs in mobile application protection?
Development fall-outs in mobile app protection often result from poor coding practices, inadequate encryption, weak authentication, and improper API security. Common vulnerabilities include hardcoded credentials, improper session handling, unprotected data storage, and lack of security testing during development. These flaws can lead to data breaches, unauthorized access, and app exploits, ultimately compromising user trust and compliance requirements.
How to check if a mobile app is secure?
To check if a mobile app is secure, perform security testing methods such as vulnerability assessments, penetration testing, and code analysis. Reviewing app permissions, ensuring data encryption, and checking for secure API calls are essential steps. Using security tools to detect malware, assessing network security configurations, and verifying compliance with industry standards further help determine an app’s security level.
What is SAST and DAST for mobile apps?
SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) are two key approaches for mobile app security testing. SAST analyzes the app’s source code, bytecode, or binaries without executing the application to detect security flaws early in development. DAST, on the other hand, tests the app in a running state, simulating real-world attack scenarios to identify vulnerabilities in runtime environments, APIs, and user interactions.
How do I check the security of an application?
To check an application’s security, conduct security audits, penetration testing, and vulnerability scans. Analyze the app’s data encryption methods, authentication mechanisms, and API security to identify potential weaknesses. Using mobile security tools like OWASP ZAP, MobSF, or Burp Suite can help detect threats. Additionally, reviewing app permissions, monitoring network traffic, and ensuring compliance with security frameworks are crucial steps.
How to test mobile apps manually?
Manual mobile app testing involves checking for vulnerabilities by performing exploratory testing, verifying authentication and authorization mechanisms, and assessing data storage security. Testers manually review the app’s behavior under different network conditions, inspect API responses, and evaluate session management. Performing input validation checks, testing for insecure data transmission, and attempting to bypass authentication are also essential steps in manual security testing.
About The Author





 Free Quote
Free Quote